To address the POODLE vulnerability, you should obviously deploy a policy that globally updates all vulnerable machines. Suppose, though, that you need to be able to make the change using the registry. Well, I’m here to hook. you. up.
Per Microsoft’s recommendation, this setting will disable SSL 3.0 and enable TLS 1.1 and 1.2 in Internet Explorer 8 and above. You can read more exciting remediation details from Microsoft if you are so inclined (https://technet.microsoft.com/en-us/library/security/3009008.aspx)!
Sooooo, this is the setting that needs to be added to the registry:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings]
“SecureProtocols”=dword:00000a80
Note: The setting above shows the hex value. If you’re using a tool that requires the value to be entered as a decimal setting (such as LANDesk), use “2688”.
For your further enlightenment, this registry change is the equivalent of making the following change to your local group policy:
- Browse to Computer Configuration -> Administrative Templates -> Windows Components -> Internet Explorer -> Internet Control Panel -> Advanced Page -> Turn off encryption support
- Change Turn off Encryption Support setting to “Enabled”
- Under Options, change the Secure Protocol combinations setting to “Use TLS 1.0, TLS 1.1, and TLS 1.2”
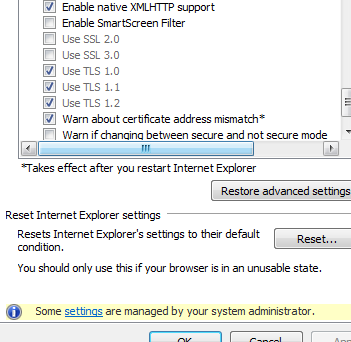
When testing this I used Windows 7 Enterprise 64-bit, but it should work with other Windows systems, as well. When the change is successfully applied, the settings should appear as follows in your Internet Options.